
Dec 15, 2025
Ultimate Guide to Donor Data Encryption
Your donors trust you with more than their money - they trust you with their personal information. Protecting this data is non-negotiable. Encryption is the key to ensuring donor data stays private and secure, even in the event of a breach. Here's what you need to know:
- Encryption Basics: Converts readable data (plaintext) into scrambled text (ciphertext) using algorithms like AES-256. Only those with the right key can decrypt it.
- Why It Matters: Legal compliance (e.g., CCPA, GDPR) and donor trust demand robust data protection. Encryption ensures stolen data is useless.
- Key Methods:
- AES-256: Secures stored data like donor records.
- Tokenization: Replaces sensitive payment info with non-sensitive tokens.
- SSL/TLS: Encrypts data during online transactions.
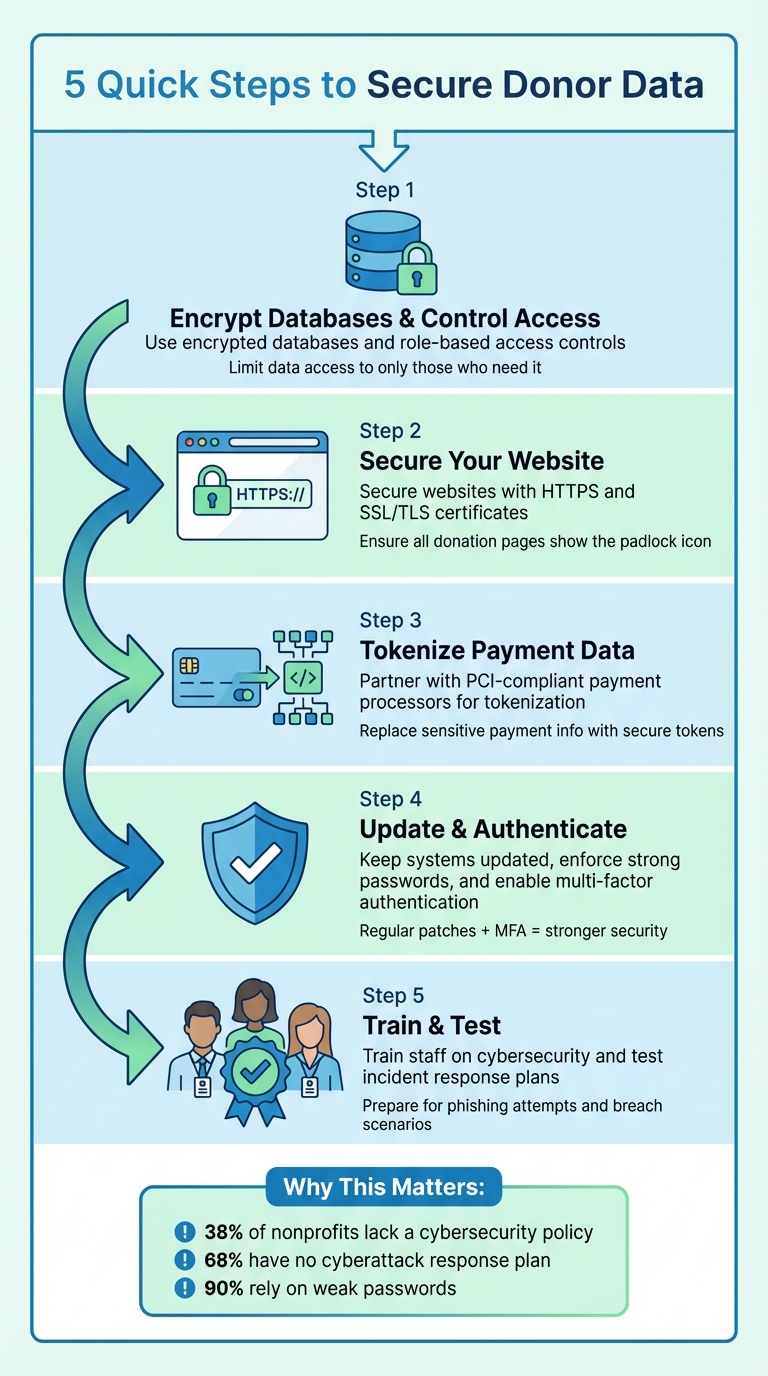
Quick Steps to Secure Donor Data:
- Use encrypted databases and role-based access controls.
- Secure websites with HTTPS and SSL/TLS certificates.
- Partner with PCI-compliant payment processors for tokenization.
- Keep systems updated, enforce strong passwords, and enable multi-factor authentication.
- Train staff on cybersecurity and test incident response plans.
Encryption isn't just about compliance; it's about showing donors their trust is well-placed. Secure their data, and you'll protect your organization's reputation and mission.
5-Step Guide to Securing Nonprofit Donor Data with Encryption
How Do Nonprofits Protect Beneficiary Data?
Encryption Methods for Nonprofits
To protect sensitive donor information, nonprofits should employ three key encryption methods: AES-256 for stored data, tokenization for payment data, and SSL/TLS for data transmission. A nonprofit best-practices guide emphasizes the importance of encrypted databases for donor information, SSL certificates for websites, and tokenization for secure money transfers. Let’s break down these methods to help safeguard your donor data.
AES-256: Protecting Stored Donor Data
AES-256 encryption is widely recognized as the gold standard for securing stored data, including donor records in databases, backups, and file storage. It works by converting sensitive information - like donor names, email addresses, and donation histories - into ciphertext that can only be accessed with the correct decryption key. This encryption method is trusted by major cloud platforms and payment systems because it’s highly effective for managing large datasets.
Nonprofits should use AES-256 at multiple levels to maximize security. For example, apply it at the device, database, and even individual field levels. This layered approach ensures that even if unauthorized access occurs, the data remains indecipherable. It’s also worth noting that U.S. federal and state privacy regulations require nonprofits to protect donors’ personally identifiable information (PII), making encryption not just a recommendation but a necessity.
Proper key management is critical for the effectiveness of AES-256 encryption. Keys should be stored separately from application servers, ideally in a dedicated key management service, and accessed only through strict role-based controls. Additionally, it’s good practice to rotate encryption keys annually or whenever a staff member with elevated access leaves the organization.
Tokenization for Long-Term Data Security
Tokenization offers a different form of protection by replacing sensitive information - such as credit card numbers and bank account details - with randomly generated tokens. These tokens hold no exploitable value outside your system. For instance, when a donor enters their payment details on a donation page, a PCI-compliant gateway replaces the card number with a token and securely stores the actual payment data in a token vault. The nonprofit’s database only retains the token and non-sensitive descriptors, like the card type or the last four digits.
This approach is especially beneficial for recurring donations and saved payment methods. Donors can set up monthly contributions without the nonprofit ever storing full card numbers, as future transactions rely solely on the token. In the event of a database breach, attackers would only gain access to tokens, which are useless without the secure token vault. Additionally, tokenization helps reduce the compliance burden associated with PCI DSS standards.
To implement tokenization effectively, nonprofits should work with a PCI-compliant payment processor that offers built-in tokenization and integrates seamlessly with their CRM or fundraising platform. Donation forms should be configured so that payment details are sent directly from the donor’s browser to the processor over encrypted channels, bypassing the nonprofit’s servers entirely.
SSL/TLS for Secure Data Transmission
SSL/TLS certificates ensure that data transmitted between donors and your website is encrypted. Donors can verify this encryption through the HTTPS protocol and the padlock icon in their browser. For donation pages, volunteer sign-up forms, event registrations, and account portals, SSL/TLS is a non-negotiable requirement for protecting donor privacy and maintaining their trust.
To ensure robust security, web servers should be configured to use TLS 1.2 or higher while disabling outdated protocols and weak ciphers. Enforcing HTTPS across your entire site - by setting up automatic redirects from HTTP to HTTPS - and obtaining certificates that cover all relevant subdomains (such as those used for donations or event pages) further strengthens your data protection efforts.
If you use third-party tools like embedded donation widgets or campaign landing pages, make sure all external assets load over HTTPS. This avoids mixed-content warnings and ensures complete end-to-end encryption for donor interactions.
How to Implement Donor Data Encryption
Implementing encryption isn’t just about picking the right tools - it’s about creating a comprehensive strategy to protect stored data, secure transmissions, and keep defenses up-to-date. Here's a startling reality: 38% of nonprofits don’t have a cybersecurity policy, 68% lack plans for cyberattacks, and 90% rely on weak passwords. These vulnerabilities highlight the importance of strong encryption and strict access controls to maintain donor trust.
Protecting Data at Rest
To safeguard stored donor information, use encrypted databases or CRMs and enforce role-based access control (RBAC) to limit access to only those who need it. Ensure that platforms provide documented encryption, PCI-compliant payment modules, and automated, encrypted backups. Schedule regular encrypted backups and test restore processes to confirm they work. Avoid storing full credit card data by using tokenization through your payment processor. Define precise roles - like development officers, finance staff, or marketing coordinators - and grant them only the access they need. Whenever possible, segment data into separate databases or schemas to keep sensitive financial information isolated from other records.
Securing Data in Transit
Make sure all pages collecting donor information use HTTPS with valid SSL/TLS certificates. Confirm that any integrated tools - such as email platforms, data warehouses, or external fundraising services - transmit donor data over encrypted channels, like HTTPS APIs or secure file transfer protocols. For staff working remotely or using public Wi-Fi, provide access through a virtual private network (VPN) to create an encrypted tunnel for secure communication. When exporting donor data for analysis or sharing with third-party vendors, anonymize or pseudonymize it by replacing names and addresses with IDs or removing direct identifiers. Always rely on trusted payment gateways that encrypt payment data during transmission and meet PCI compliance standards. Once secure transmission is in place, maintain protection through regular monitoring and strict access controls.
Maintenance and Access Controls
Keep all systems - such as donor databases and plugins - updated with the latest patches. Require strong, unique passwords and enforce multi-factor authentication (MFA) across all critical systems, including donor databases, cloud CRMs, email, and payment platforms. This reduces the risk of unauthorized access. Conduct regular security audits, run vulnerability scans, and use log monitoring with alerts to detect suspicious activity. Train staff on cybersecurity basics, like spotting phishing attempts and securely handling donor data exports. Finally, develop and test an incident response plan that outlines clear steps, communication protocols, and recovery measures to handle breaches effectively.
sbb-itb-deea482
Advanced Encryption Strategies
Once your encryption framework is solid, there are additional strategies that can take donor data security to the next level. These go beyond basic encryption, incorporating payment compliance protocols, regular vulnerability assessments, and comprehensive security architectures.
PCI Compliance for Payment Security
The Payment Card Industry Data Security Standard (PCI DSS) sets strict guidelines for organizations handling cardholder data. For nonprofits accepting online donations, meeting these standards is non-negotiable - it’s a safeguard for both the organization and its donors against fraud.
Compliance involves several key practices, such as avoiding the storage of full card numbers or CVV codes unless absolutely necessary, implementing tokenization, and ensuring secure handling of sensitive data. Additional measures include enforcing strong passwords, adopting multi-factor authentication, keeping software updated, and conducting routine vulnerability scans and penetration tests.
To simplify compliance, many nonprofits outsource card processing to certified payment gateways. These gateways handle sensitive information using tokens and masked details, reducing the organization’s PCI scope. By combining this approach with other advanced security measures, nonprofits create a well-rounded and effective protection strategy.
Security Audits and Penetration Testing
Regular security audits and penetration tests are essential for ensuring that encryption measures hold up under real-world conditions. Penetration tests simulate cyberattacks to uncover weaknesses in web applications, APIs, and network systems.
For larger nonprofits, it’s a good practice to conduct quarterly external vulnerability scans on internet-facing systems, along with annual internal scans and penetration tests. Organizations handling payment data may also need scans from a PCI Approved Scanning Vendor and compliance reports from a Qualified Security Assessor.
Incorporating these audits into governance routines - such as quarterly board or finance committee meetings - can help keep security efforts on track. Tracking key security metrics ensures that vulnerabilities are identified and addressed promptly, maintaining a proactive stance against potential threats.
Integrated Solutions with Share Services
Managing encryption, PCI compliance, and security audits can become overwhelming, especially for mid-sized nonprofits with annual revenues between $1 and $20 million. Share Services offers a streamlined solution by centralizing security management and reinforcing donor trust.
Their integrated donor engagement programs utilize secure CRMs and fundraising platforms equipped with encryption, tokenization, and SSL/TLS protocols. Share Services also supports role-based access controls, multi-factor authentication, and disciplined data-retention policies. They ensure timely security patches and provide compliance reports, allowing nonprofits to focus on building stronger donor relationships instead of juggling technical security tasks. This holistic approach simplifies complex processes, making robust data protection more manageable for growing organizations.
Compliance and Transparency
Legal Requirements for Nonprofits
Nonprofits in the U.S. that handle donor data must adhere to strict legal standards to protect personally identifiable information (PII). Federal and state laws demand safeguards like encryption, controlled access, and secure payment systems to ensure donor data stays protected. For organizations collecting data from California residents, the California Consumer Privacy Act (CCPA) sets specific rules. These include encrypting sensitive information and giving donors rights such as deleting their data or opting out of data collection.
If your nonprofit processes credit or debit card donations, compliance with PCI DSS is non-negotiable. This standard focuses on encrypting cardholder data and ensuring secure transmission. States like New York and Massachusetts also have their own data protection laws, which emphasize secure storage and regular audits to maintain compliance.
Having a written encryption policy is essential - not just for legal compliance but also to demonstrate accountability to regulators, auditors, and donors. Your policy should cover key areas like encryption methods (e.g., AES-256 for databases, SSL/TLS for data transmission), access controls such as multi-factor authentication, data retention schedules, and audit procedures. This documentation is invaluable during audits for CCPA or PCI compliance and ensures staff are trained to follow best practices. By meeting these legal standards, nonprofits build a strong foundation for transparent and trustworthy operations.
Building Trust Through Transparency
Legal compliance is just the starting point. To earn and maintain donor trust, nonprofits need to clearly communicate how they handle personal data. Donors today expect transparency about how their information is collected, stored, encrypted, shared, and retained.
A great way to achieve this is by publishing a clear privacy policy on your website and donation forms. Use plain, accessible language - for example, "We use AES-256 encryption to protect your data and secure it with multi-factor authentication." Avoid overwhelming donors with technical jargon. Offer straightforward opt-out options and respect donor preferences regarding how often and through which channels they want to be contacted. Practices like buying or selling donor lists can quickly damage trust and should be avoided.
If you work with fundraising partners or technology providers, be upfront about those relationships. Make sure any contracts with third parties require adherence to encryption and data protection standards. Transparency isn’t just a way to prevent problems - it’s a smart fundraising tactic. When you openly share your privacy practices and honor donor choices, you strengthen relationships, boost donor retention, and show that your organization values both its mission and the people who support it.
Conclusion
Encrypting donor data isn’t just a technical choice - it’s a core responsibility for every nonprofit handling personal and payment details. Effective encryption protects databases, secures online transactions, and ensures that donor information remains unreadable even in the event of a breach. This layer of security not only safeguards donor trust but also ensures compliance with federal and state privacy laws, meeting essential regulatory standards.
To achieve this, nonprofits should take specific steps: encrypt data at rest using AES-256, secure donation pages with SSL/TLS certificates, and adopt PCI-compliant tokenization. Combine these measures with role-based access controls, multi-factor authentication, and well-defined data protection policies to build a robust security framework.
For nonprofits with limited in-house security expertise, external support can make all the difference. Organizations with annual revenues between $1 million and $20 million can collaborate with specialists like Share Services to implement encryption best practices across campaigns and donor interactions. This ensures that as online giving grows, security measures remain a step ahead.
Equally important is transparency. Clearly explaining encryption practices in plain language on donation pages and privacy policies reassures donors that their data is treated with the same care as their contributions. This builds stronger donor relationships, reduces regulatory risks, and reinforces your nonprofit’s reputation as a trustworthy steward of sensitive information.
Encryption isn’t just a back-office function - it’s integral to ethical fundraising and long-term organizational success. By prioritizing these practices, nonprofits can secure donor trust and ensure their mission thrives for years to come.
FAQs
What’s the difference between AES-256 encryption and tokenization for protecting donor data?
AES-256 encryption secures donor information by converting it into unreadable code using a 256-bit key. This method is incredibly resistant to brute-force attacks because only the correct key can decrypt the data, ensuring it stays safe from unauthorized access.
Tokenization, on the other hand, works differently. Instead of encrypting the data, it replaces sensitive information with unique, non-sensitive tokens. These tokens hold no value if intercepted and are linked back to the original data through a secure token vault. By reducing the amount of sensitive data stored, tokenization lowers the risk of exposure in the event of a breach.
In short, AES-256 encryption scrambles data to protect it, while tokenization replaces it entirely. Depending on your organization's specific needs, both methods can offer robust security for donor information.
What steps can nonprofits take to comply with data protection laws like GDPR and CCPA?
Nonprofits can navigate data protection laws like GDPR and CCPA by following essential practices to keep donor information secure. Start with strong encryption to safeguard sensitive data, whether it's being transferred or stored. Additionally, having clear and transparent privacy policies is crucial. These policies should explain how donor data is collected, stored, and used in a way that's easy to understand.
Another important step is obtaining explicit consent from donors before collecting any personal information. Regular audits of your data management processes can help uncover and fix potential weaknesses. Limiting access to sensitive data to only authorized personnel further reduces risks. Not only do these measures help ensure compliance with regulations, but they also strengthen donor trust in your organization.
Why should nonprofits use a PCI-compliant payment processor for tokenization?
Using a PCI-compliant payment processor that supports tokenization comes with several important advantages. By substituting sensitive card details with secure tokens, it significantly reduces the risk of fraud and unauthorized access. This method also simplifies your nonprofit's efforts to meet PCI DSS compliance requirements, cutting down on the complexity of adhering to industry standards.
Another major benefit is the ability to build trust with donors. Protecting their payment information reassures them that their data is safe, which is crucial for fostering long-term support. On top of that, streamlined payment processes enhance the overall donor experience, allowing your organization to stay focused on its mission while keeping data security intact.
Related Blog Posts
Get helpful resources, straight to your inbox
We love sharing tools, ideas, and stories that make nonprofit work a little lighter and a lot more effective. Sign up below and we’ll send you practical tips, free resources, and a bit of encouragement—because the work you’re doing matters.
No spam. Just good stuff for good people.
.svg)